Changes you can make to Zoom settings for greater privacy and to block Zoombombing
You’re not ready to know all that Google and Facebook know about us
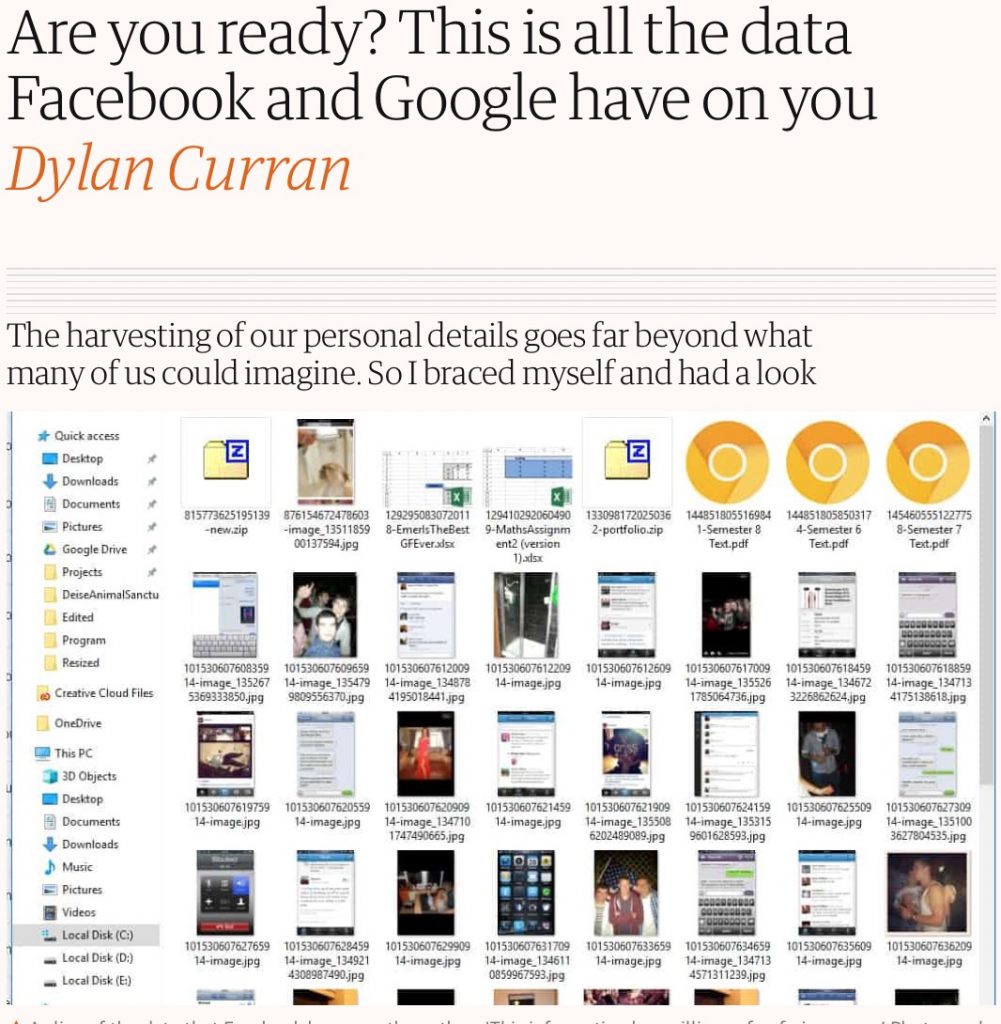
It’s awe-inspiring and terrifying to know how much Google and Facebook know about us: where we go, what time we go to the gym, what you’ve searched, what searches you’ve deleted, what apps you use, what you and your friends talk about, and more. Dylan Curran, writing in The Guardian, says,
They can access your webcam and microphone
The data they collect includes tracking where you are, what applications you have installed, when you use them, what you use them for, access to your webcam and microphone at any time, your contacts, your emails, your calendar, your call history, the messages you send and receive, the files you download, the games you play, your photos and videos, your music, your search history, your browsing history, even what radio stations you listen to.
Online privacy advice via The New York Times, Wired and Forbes
From Participant Media: “Several media outlets are rounding up privacy advice. Here’s how you can protect your phones, computers, TVs and more via The New York Times, Wired and Forbes.”
@NYTimes: Protect against on-line surveillance by updating your devices often
@Wired (video): How to Protect Your Privacy
@Forbes: Here’s How The CIA Allegedly Hacked Samsung Smart TVs – And How To Protect Yourself
Blogger Bob Braun rips testing giant Pearson’s privacy invasion practices wide open
 With amplification from Diane Ravitch (where you can also read the text of Bob’s original post if his website is still inaccessible), Washington Post, Daily Kos, a growing number of local news portals and now The War Report radio show, Bob Braun has busted wide open the practice of standardized testing giant Pearson Education to spy on and oppress students using Pearson Streamlines Social Media Listening and Monitoring With Tracx. It’s more than shocking.
With amplification from Diane Ravitch (where you can also read the text of Bob’s original post if his website is still inaccessible), Washington Post, Daily Kos, a growing number of local news portals and now The War Report radio show, Bob Braun has busted wide open the practice of standardized testing giant Pearson Education to spy on and oppress students using Pearson Streamlines Social Media Listening and Monitoring With Tracx. It’s more than shocking.
Bob Braun’s Ledger reported the exclusive story that Pearson is monitoring students’ social media accounts during PARCC testing … and that both Pearson and the NJDOE called for the punishment of a student who had tweeted after taking the test, although school authorities knew – and had reported – that the student did not share any sensitive information. This Watchung Regional High School District Superintendent’s letter was leaked to Braun and started the snowball rolling.
What incensed Diane Ravitch and motivated her to immediately publicize Braun’s March 13 scoop was the Denial of Service (DOS) attack that was launched to disable Braun’s blog while server administrators scrambled to engage protocols to shut the attack down and make the site accessible again. How do we know that the problem was a DOS attack and not simply a lot of interest in reading Braun’s post? Because Braun’s web host contacted him and said so. Braun explains:
Bob Braun’s Ledger is back up but is still very slow. It’s probably easier to get to it through something other than Facebook. Initially, I thought–vainly– the site was acting up because of the number of people reading it. Then I got an email from my webhost saying the site was under a “denial of service” attack.
The webhost itself then suspended the site to stop the attacks and to give it time to repair the problem and install fixes to prevent future attacks. It seems to have come back up–for now–but clearly someone wanted it down. I’m flattered. And I am so grateful to all of those I know and do not know who sent messages of support and got around the siege by posting PDFs of the original blog. Ironically, I have not been a vocal anti-PARCC or anti-Common Core voice. But the idea that a global corporation and a state agency would cooperate to entrap children in their schemes chills me to my very old bones. What makes it worse is the indifference of the mainstream media and, of course, the thuggery represented by trying to destroy what was a very straight news story. I know distinctly what side I’m on now. Stop the corporate spies and their collaboration with government. Refuse the test. I do not believe in conspiracy theories but I do believe in conspiracies and this is one helluva big one.
Discontent with Pearson is growing and hard questions are increasingly being directed at state governments that support and fund them. On 04 March 2015, Eric Kiefer of the Patch reported a protest by
…a coalition of education, labor and community advocates (protested) the $83 million tax break the corporate giant received from the NJ Economic Development Authority (NJ EDA) for moving 628 employees from Bergen County to Hudson County.
NJ Working Families points out that those $83M dollars were spent for nothing, as after the move Pearson took 600 jobs to New York City.
This afternoon at 5pm EST on Sun 15 March 2015, you can catch Braun on air with Dr. James Miller of the War Report discussing the dawning revelation of Pearson as the Orwellian Big Brother in American public education.
What can we do to fight back?
Hungry for privacy? Facebook de-friending won’t even get you close

I’ve been really thinking about a Facebook friend’s earlier post, saying she feels exposed by having 822 friends and will start deleting some in order to get more privacy. I just had to reply to the privacy issue and afterwards, realized that my assertions needed to be backed up by reliable data. “I must say,” I commented to my friend, “I find it strange that you would play a game on Facebook or post anything here and voice concerns about privacy,” and followed that with my first information point: “Facebook sells your data to game creators – this is a well-known fact.”
Some of the most widely used apps on Facebook —the games, quizzes and sharing services that define the social-networking site and give it such appeal—are gathering volumes of personal information. Source: Wall Street Journal
I continued, “Facebook also has ties to the federal government and is probably selling all of our data to the feds – or just giving it away.”
Facebook’s most recent round of funding was led by a company called Greylock Venture Capital, who put in the sum of $27.5m. One of Greylock’s senior partners is called Howard Cox, another former chairman of the NVCA, who is also on the board of In-Q-Tel. What’s In-Q-Tel? Well, believe it or not (and check out their website), this is the venture-capital wing of the CIA. Source: Dennis Howlett on ZDNet.com quoting Guardian Unlimited writer Tim Hodgkinson.
Bet you didn’t know the CIA has a venture capital wing. Wikipedia tells us about In-Q-Tel:
Former CIA director George Tenet says, “We [the CIA] decided to use our limited dollars to leverage technology developed elsewhere. In 1999 we chartered … In-Q-Tel. … While we pay the bills, In-Q-Tel is independent of CIA. CIA identifies pressing problems, and In-Q-Tel provides the technology to address them. The In-Q-Tel alliance has put the Agency back at the leading edge of technology … This … collaboration … enabled CIA to take advantage of the technology that Las Vegas uses to identify corrupt card players and apply it to link analysis for terrorists [cf. the parallel data-mining effort by the SOCOM-DIA operation Able Danger], and to adapt the technology that online booksellers use and convert it to scour millions of pages of documents looking for unexpected results.[6]”
In-Q-Tel sold 5,636 shares of Google, worth over $2.2 million, on November 15, 2005.[7] The stocks were a result of Google’s acquisition of Keyhole, the CIA funded satellite mapping software now known as Google Earth.
As of August 2006, In-Q-Tel had reviewed more than 5,800 business plans, invested some $150 million in more than 90 companies, and delivered more than 130 technology solutions to the intelligence community.[4][8] In 2005 it was said to be funded with about $37 million a year from the CIA.[9]
On top of this, you’re caught on camera (as we all are) many times every day, every time we go anywhere .. even locally.
In Big Brother Britain there is an incredible one CCTV camera for every 32 citizens, a study has revealed … The revelation that 1.85 million cameras are watching our every move confirms the shocking extent of surveillance in 21st century Britain. Source: The Daily Mail (UK)
…pushes to use new surveillance tools in law enforcement are supported with federal dollars Source: New York Times
Even when you’re driving, by Automatic license plate readers. Check out this interactive slideshow that tells the story:
The police are tracking you by license plate and keeping that information for years:
D.C. police are aggressively using small cameras to scan hundreds of millions of license plates annually, storing the images in a database for two years even if the driver is not suspected of having committed any crimes. Source: American University Radio
Mr. Katz-Lacabe isn’t charged with, or suspected of, any crime. Local police are tracking his vehicle automatically, using cameras mounted on a patrol car that record every nearby vehicle—license plate, time and location … “Why are they keeping all this data?” says Mr. Katz-Lacabe, who obtained the photos of his car through a public-records request. “I’ve done nothing wrong.” Source: New Tracking Frontier: Your License Plates
And we’re not only being tracked by government! Private contractors are capturing billions of photos of cars’ license plates, information which they sell to private and government buyers:
Privately owned license-plate imaging systems are popping up in upstate New York — in parking lots, shopping malls and, soon, on at least a few parts of the New York state Thruway. Most surprisingly, the digital cameras are mounted on cars and trucks driven by a small army of repo men … At present that database has 2.3 billion permanent records. Source: License Plate Data Is Big Business (USA Today 02 Nov 2014)
Where we go and who we spend time with is also being monitored by our phone’s GPS signals:
All cell phones register their location with cell phone networks several times a minute, and this function cannot be turned off while the phone is getting a wireless signal. The threat to personal privacy presented by this technology is breathtaking … federal appeals court in Washington, D.C. explained: “A person who knows all of another’s travels can deduce whether he is a weekly church goer, a heavy drinker, a regular at the gym, an unfaithful husband, an outpatient receiving medical treatment, an associate of particular individuals or political groups — and not just one such fact about a person, but all such facts.” Source: Cell Phone Location Tracking Public Records Request (ACLU)
But I got the piece about GPS monitoring capability wrong, “…part of why it’s illegal in the US these days to sell a phone that lacks GPS capability.” That won’t actually be illegal until 2019, by which time mobile phone providers will be required to either provide GPS tracking for both phones and VOIP devices – or be able to do a very sophisticated location pinpointing service of personal communication devices via triangulation, something their current equipment can’t handle well enough:
No date was given for when non-GPS enabled devices must be discontinued, but given FCC estimates that by 2018, 75 percent of all mobile devices will be GPS capable, it is likely that the assumption is the sunsetting of obsolete devices will occur naturally as consumers chuck outdated gadgets for shiny new ones. Source: Tom’s Guide
I added a couple of extra thoughts for my friend to think on, which seem worth sharing here too: “If you want privacy, it’s going to take quite a bit more than unfriending some Facebook people to get it … just throwing in my 2¢ there for what they’re worth (about 2¢, I’m guessing). I know I probably just increased my chances of getting the axe (note: unfriended) by about 4000% but I couldn’t help myself.” And this is true. Privacy is way too important an issue for us to be either quiet over or misinformed about.
More on privacy:
![]() ACLU Publication: You Are Being Tracked
ACLU Publication: You Are Being Tracked
Many Cameras, Little Privacy ©2013 Washington Post
Did Facebook illegally try to depress users?
 I learned today that Facebook is under an FCC consent decree that will last 20 years (until 2032) to protect user’s privacy. Also that privacy advocacy group EPIC has filed a formal complaint against Facebook for violating it. Facebook recently attempted to influence the mood of 700,000 users by filtering posts in their News Feeds to show either more good or more bad news, and then monitored individual users’ posts for words known to reflect emotional state. This was a research project that involved Cornell University but users were not informed that it was taking place.
I learned today that Facebook is under an FCC consent decree that will last 20 years (until 2032) to protect user’s privacy. Also that privacy advocacy group EPIC has filed a formal complaint against Facebook for violating it. Facebook recently attempted to influence the mood of 700,000 users by filtering posts in their News Feeds to show either more good or more bad news, and then monitored individual users’ posts for words known to reflect emotional state. This was a research project that involved Cornell University but users were not informed that it was taking place.
Scientist Jaron Lanier in his New York Times Op-Ed piece, says social network researchers must do better and cautions that depression can lead to suicide so inducing it without consent and screening procedures is a very bad idea:
It is unimaginable that a pharmaceutical firm would be allowed to randomly, secretly sneak an experimental drug, no matter how mild, into the drinks of hundreds of thousands of people, just to see what happens, without ever telling those people.
Take control of your privacy & end surveillance

Jon Fox, Global Advocacy Manager for Access points out that we have the power as individuals to curtail mass surveillance and data collection and comments, “Here are four things you can do today to keep your online activities private and secure from snooping eyes.”
1. Secure Browsing: Access recommends using the Tor Browser Bundle which provides access to blocked websites, and prevents others from tracking you online or watching what sites you visit by obscuring your online communications. Tor also prevents websites and others from collecting data on you – most importantly your physical location.
2. Secure Email: The most popular way to encrypt your email communications is using Pretty Good Privacy (PGP), most accessible through its open source version, Gnu Privacy Guard (GPG). For help installing GPG, follow Security in a Box’s walkthrough, which covers Windows, Mac OSX, and Gnu/Linux operating systems. They even have instructions on how to install and use GPG on Android.
3. Secure Search: Search data generated by using Google, Yahoo, or Bing are all stored and can be accessed upon request by state authorities. Unlike these search engines, StartPage (also available as a mobile app for Android and iOS) and DuckDuckGo (mobile app for Android and iOS) do not collect personal information on users; they don’t keep a history of your searches, use cookies, or store your IP address.
4. Secure Chat: Jitsi is a cross-platform, free and open-source encrypted instant messaging, voice, and video chat program and is available for Microsoft Windows, Mac OS,and Linux. It supports many of the most popular instant messenger services, including Facebook, Google Talk, AIM, ICQ, MSN, and Yahoo! Messenger. For web-based secure video chat, Jitsi Meet is a free and open-source solution for the latest versions of Mozilla Firefox, Google Chrome, and Chromium web browsers.
Where does Google Voice fit into the privacy spectrum these days?
 Being gifted a spectacular MotoX Adroid phone from my brother saddled me with the obligation to sort through privacy options I had avoided confronting until now by staying away from smart phones and as much as possible, the public observation grid. I use a client-side email application connected to a private email service, which means my mail isn’t being stored on Yahoo or Google’s servers or monitored by them (as most people’s e-correspondence is). And I use a client-side calendar as well NOT synched via the cloud, which is another layer of privacy protection I’ve got that many people gave up a long time ago.
Being gifted a spectacular MotoX Adroid phone from my brother saddled me with the obligation to sort through privacy options I had avoided confronting until now by staying away from smart phones and as much as possible, the public observation grid. I use a client-side email application connected to a private email service, which means my mail isn’t being stored on Yahoo or Google’s servers or monitored by them (as most people’s e-correspondence is). And I use a client-side calendar as well NOT synched via the cloud, which is another layer of privacy protection I’ve got that many people gave up a long time ago.
I’m aware that when I leave home, I’m being visually recorded by dozens of cameras. And when I drive anywhere my license plate is being scanned and tracked by a network of millions of devices. I know that my EZ-Pass device is scanned in places other than toll booths and that big box retailers can follow me around their stores via my phone‘s wifi signal …
 By minimizing mobile phone use, driving and by staying away from retail spots I hoped to retain some semblance of privacy in my life and possibly, I have. But with the acquisition of this slender, miniature supercomputer I now tote around in my breast pocket, my privacy bubble has been completely burst. As long as I carry around with me the full-blown communication system which this brilliant phone represents in an internet connected world, I will have so much less privacy going forward than I did before December 20, 2013 when my brother put the power of the MotoX in my hand.
By minimizing mobile phone use, driving and by staying away from retail spots I hoped to retain some semblance of privacy in my life and possibly, I have. But with the acquisition of this slender, miniature supercomputer I now tote around in my breast pocket, my privacy bubble has been completely burst. As long as I carry around with me the full-blown communication system which this brilliant phone represents in an internet connected world, I will have so much less privacy going forward than I did before December 20, 2013 when my brother put the power of the MotoX in my hand.
This is actually a gift I requested as at the level of activism my family practices today we need to be both mobile as well as constantly connected. So believe me, I’m not complaining. I’m just learning how to best reconcile my profound longing for privacy in a world in which this is a constantly diminishing resource. I’m reconciled with most of the privacy concessions I’m needing to make but there is one major issue I haven’t been able to clear up yet.
I have a Google Voice number that I would like to use as my Android phone’s outgoing number (the number that will show up in Caller ID when someone gets a call from me). But I haven’t been able to figure out … if I place calls using Google Voice as my outgoing call provider, is Google going to record, mine and store my entire conversations?
I was able to learn that Google records that I place calls and to whom they are made, a standard practice today which comes as no surprise to any literate person since Snowden whistleblew on the NSA’s data collection protocol last year. I also learned that Google won a patent award (which it claims not to be using yet) for mining “environmental data” from phone conversations. Meaning, Google owns the technology to listen for words in conversations placed over its network which will indicate whether a storm is brewing (in order to sell rain gear and generators) or if the weather will be fine (in order to promote trips to the beach and picnic baskets).
However, I still don’t know if Google is recording and archiving the actual, full voice phone conversations of the calls placed over its Google Voice network. I would find it very convenient to use Google Voice for my outgoing phone calls but first, I would really like to know how much more privacy I’ll be giving up if I do.
Please help a sister out if you know the answer.
Be vigilant in the twilight against oppression & loss of privacy
As nightfall does not come at once, neither does oppression. In both instances, there is a twilight when everything remains seemingly unchanged. And it is in such twilight that we all must be most aware of change in the air, however slight, lest we become unwitting victims of the darkness.
Supreme Court Justice William O. Douglas
UK’s Mail Online reported
We must keep the internet open
Several authoritarian regimes reportedly would ban anonymity from the Web, which would make it easier to find and arrest dissidents. Others have suggested moving the privately run system that manages domain names and Internet addresses to the United Nations. …
When I helped to develop the open standards that computers use to communicate with one another across the Net, I hoped for but could not predict how it would blossom and how much human ingenuity it would unleash. What secret sauce powered its success? The Net prospered precisely because governments — for the most part — allowed the Internet to grow organically, with civil society, academia, private sector and voluntary standards bodies collaborating on development, operation and governance.
In contrast, the I.T.U. creates significant barriers to civil society participation.
Fight for internet freedom and the open web
- Free Press
- Electronic Frontier Foundation
- Electronic Privacy Information Center
- Lawrence Lessig, Harvard Law Professor, who’s spending his life educating America about how disconnected American politicians have become from the American people and why we should take big money out of public elections: 28 Oct 2011 lecture
- and book, Republic, Lost: How Money Corrupts Congress–and a Plan to Stop It
Who Has Your Back on The Web?
Friends, we have an ongoing need to educate ourselves about what privacy means in the Internet environment and take action to protect it. The Internet “space” we live in today is a pioneering world where people’s rights haven’t yet been fully determined. The EFF is one of the organizations the general public knows little, or nothing, about which is working behind the scenes every day at no charge to us to protect the privacy of all netizens. Other organizations are the ACLU and Public Citizen.
Urging our Internet access and social media providers to stand with us when the government knocks on their door and demands information about us is one way we can advocate for protecting our privacy. EFF challenges Internet providers to stand with us with their Who Has Your Back Campaign. The EFF asks:
When you use the Internet, you entrust your online conversations, thoughts, experiences, locations, photos, and more to companies like Google, Yahoo and Facebook. But what happens when the government asks these companies to hand over your private information? Will the company stand with you? Will it tell you that the government is looking for your data so that you can take steps to protect yourself?
Start protecting your Internet privacy rights by signing the Who Has Your Back campaign petition and asking your friends and family to sign too.
About the EFF – in their own words
The Electronic Frontier Foundation is the leading organization protecting civil liberties in the digital world. Founded in 1990, we defend free speech online, fight illegal surveillance, promote the rights of digital innovators, and work to ensure that the rights and freedoms we enjoy are enhanced, rather than eroded, as our use of technology grows.
Blending the expertise of lawyers, policy analysts, activists, and technologists, EFF achieves significant victories on behalf of consumers and the general public. EFF fights for freedom primarily in the courts, bringing and defending lawsuits even when that means taking on the US government or large corporations. By mobilizing more than 61,000 concerned citizens through our Action Center, EFF beats back bad legislation. In addition to advising policymakers, EFF educates the press and public.
EFF is a member-supported organization. Find out more at
Hide your list of email recipients
There are good reasons to hide recipient’s addresses when you sent an email broadcast. Here are a few to think about:





